The fact that cars are a target to hackers is not surprising. Discovering a vulnerability in a car brings fame to ethical hackers, while unethical hackers can sell their finding to automotive gangs. One of the examples is vulnerability tracked as CVE-2022-27254, which affects many modern Honda cars.
The vulnerability allows an attacker with the ability to capture the unlock radio signal sent from a key fob to remotely unlock the car. No expensive hardware is necessary, the only thing needed is a device worth a couple of hundreds of dollars, that is capable of capturing and re-transmitting radio signals. Such devices are legal and publicly available for research and educational purposes.
We prepared a video about a use of such device in real-world:
After capturing the unlock signal, the attacker can store it and use it at will. The vulnerability stems from the lack of a technique called rolling codes. It means that each time you unlock your car, the same unlock signal is sent to unlock the car. Capturing and re-using this signal is called a replay attack in expert terminology.
Replay attack, in general definition, means capturing information and re-using it later in a malicious way. Typical example is capturing a hash of a password during authentication (hash is an output of a one-way formula) and then re-using it later to log in.
One of the techniques to mitigate replay attacks is rolling codes. Rolling codes are supposed to make attackers life significantly harder, as captured code cannot get directly re-used. The concept of rolling code means that a different signal is sent with each successful unlock. Car expects new values based on an internal counter that’s keeping track of all the unlocks. Implementing rolling codes is considered best practice with remotely unlocked devices, such as cars.
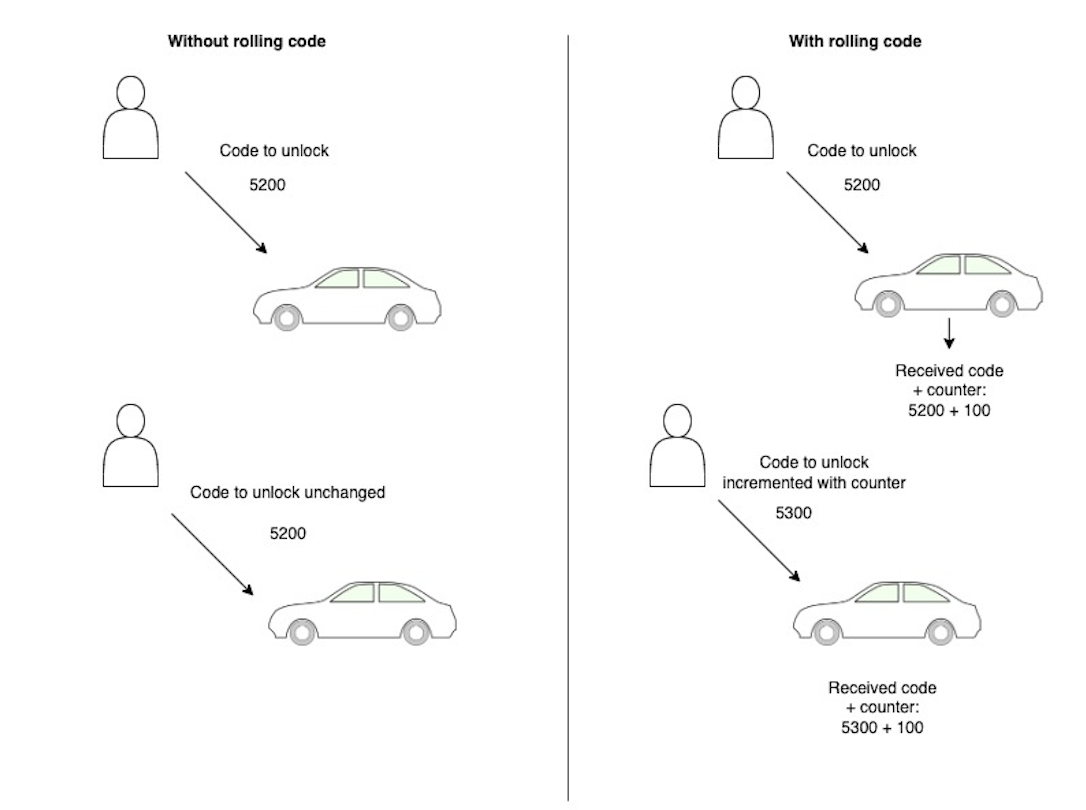
Figure 1. A simple visualization of rolling codes.
The vulnerability affects Honda vehicles made in model years 2016 to 2020. Honda responded with no intentions to fix the vulnerability of those vehicles, leaving owners worried. The only way to protect yourself is to start using physical keys and placing your key fob into a Faraday cage after each use.
