In this overview we introduce the selection of the most used and most usable malware analysis tools. Moreover, we select the tools which are freely available.
Malware analysis conststs of several phases, starting with extraction and investigation of basic info based on malware sample’s metadata, continuing with behavioral analysis and ending with debugging and reverse engineering of the sample. Depending on requirements and approach, malware analyses can take several hours and we often need to use tens of tools.
The purpose of this post is not to present long list of every available malware analysis tool. Instead, we would like to present the selection of tools useful for both beginners and experienced analysts. Moreover, the presented tools are available for free, either as open source or freeware (however, in some cases, only for non-commercial usage). Thus, even students, graduates and enthusiasts can afford them for hobby malware analysis.
IDA Freeware
IDA is probably the most recognized disassembler (a computer program that translates machine language into assembly language) and one of the most used tools among the professionals. Freeware version is available, too, however, it comes with several limitations - it supports only 32-bit and 64-bit applications for x86 and x64 CPUs. Support for plugins and scripting is also limited - for example, very popular plugin for IDA Python is missing. For scripting, there is available only IDC language.
On the other hand, for study and research purposes there is a free version of popular Hex-Rays x64 decompiler in version 7.6. While the decompiler is only a cloud-based decompiler, the previous versions did not offer such a feature and even users with Pro license of IDA had to buy separate license for Hex-Rays decompiler. Therefore, many analysts used (and still use) alternate disassemblers with support for decompilation - Cutter (frontend for the Radare2 or Rizin framework) and Ghidra, open source framework for reverse engineering by NSA.
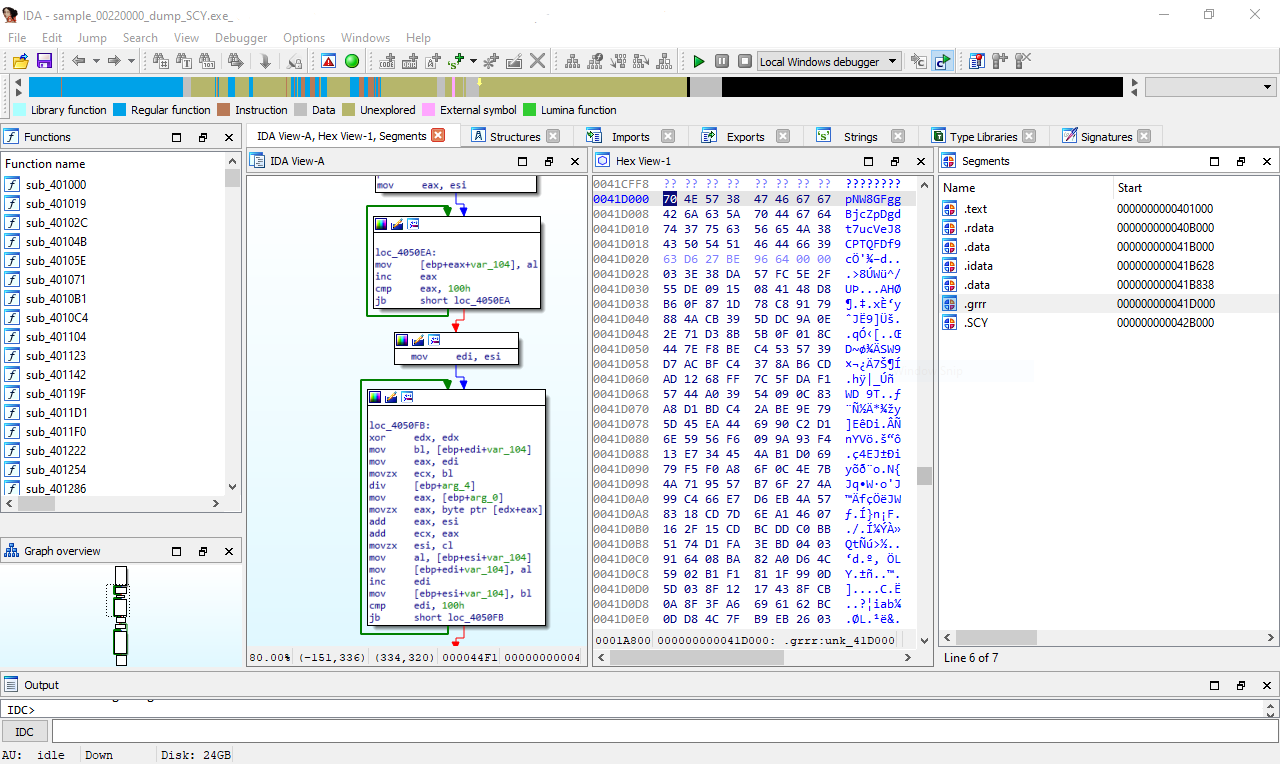
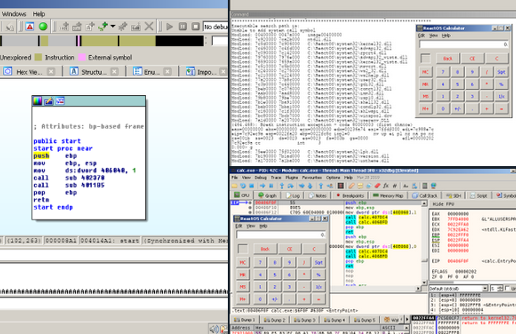
Fig. 1: IDA Freeware and decryption of the REvil ransomware’s configuration
x64dbg
An open source debugger for Windows. It supports both 32-bit and 64-bit programs fpr x86/x64 CPUs. Its user interface is similar to the well-known layout of OllyDbg a Immunity Debugger, while it offers several improvements. It integrates the Graph View of basic code blocks and it supports the Snowman decompiler as a plugin, too. In addition, there are many plugins which are suitable for more experienced analysts.
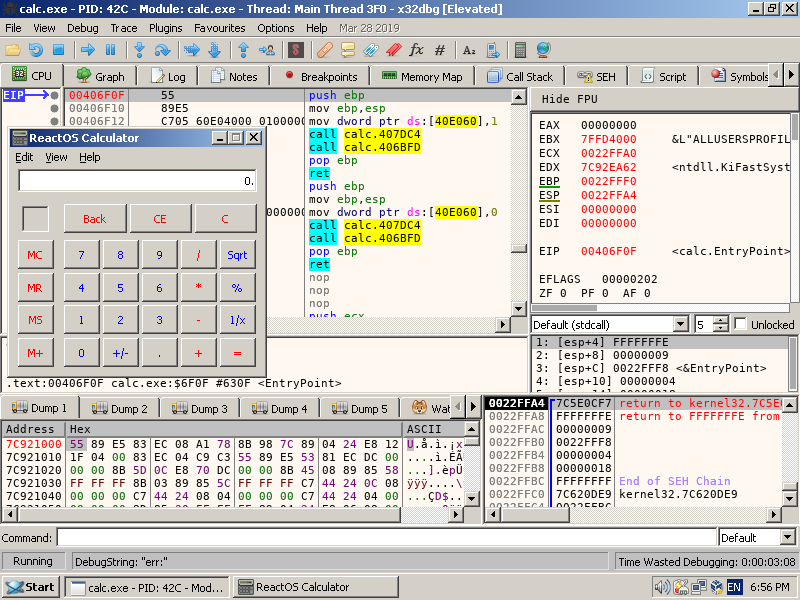
Fig. 2: x64dbg a debugging the Calculator in ReactOS
Hiew
Hexadecimal editor Hiew, which name is an abbreviated form of the Hacker’s View. It can look little bit old-school, but its features are worth a try, especially for quick analysis of portable executable files. It offers three modes of view - text, hexadecimal and disassembly. It can view and edit headers, it understand the structure of PE file format, it can extract text strings and it contains several features very useful for analysis of obfuscated files - for example, it can transform blocks of data with xor or it can apply more complex transformations.
Demo version is available for free, but full version (without updates) is definitely not expensive ($19 on english website, approx. $7 on russian website).
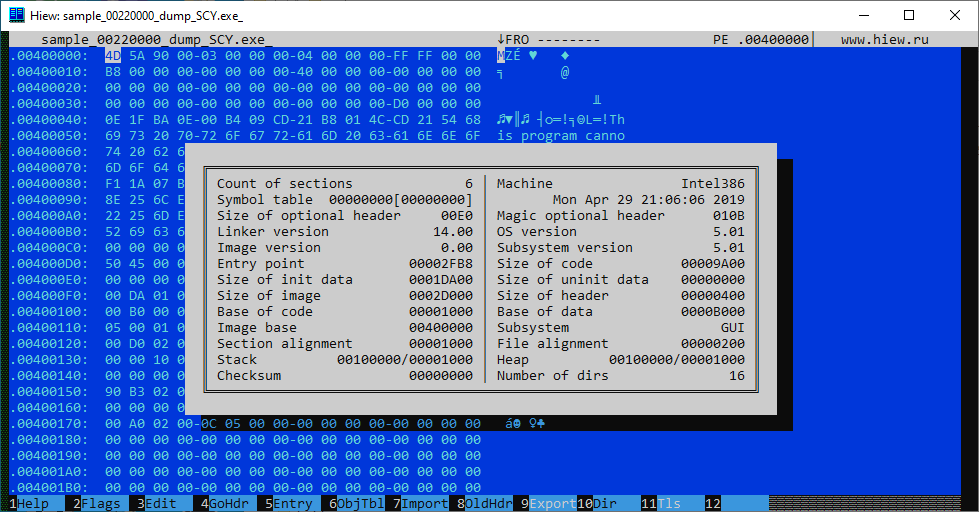
Fig. 3: Hiew and PE header of REvil ransomware
Process Hacker
Process Hacker is similar to Process Explorer (from Windows Sysinternals), it is an advanced task manager, with lot of improvements for monitoring system resources, debugging software and detecting malware. It can view properties of processes, running threads, call stack, opened files and handles, extract text strings from the process memory. Moreover, it can manipulate with running processes, for instance it can suspend them, dump the process memory, and many more.
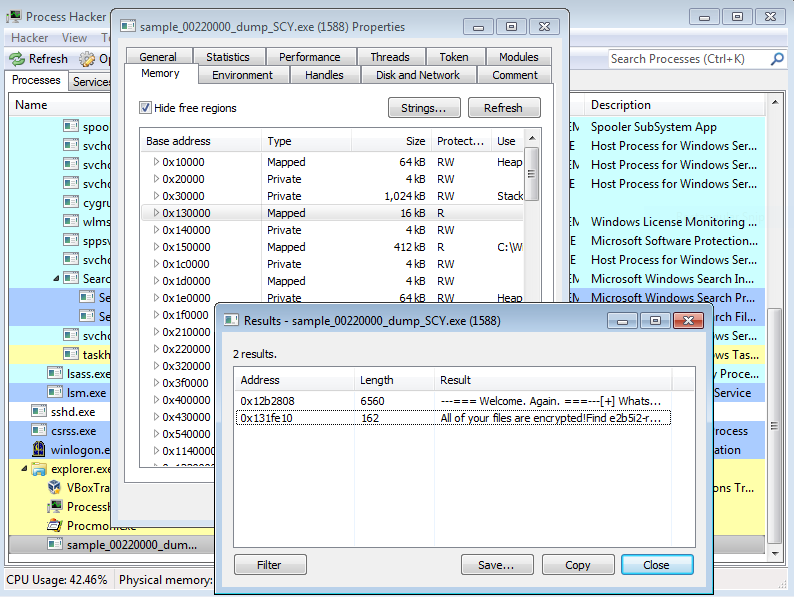
Fig. 4: Process Hacker and extracted text strings from the REvil ransomware process memory
Process Monitor
Process Monitor, or ProcMon, from Windows Sysinternals is suitable tool for behavioral analysis and monitoring the active processes, especially the filesystem and registry activity, network activity and events related to processes and threads. It offers powerful filtering of events based on several parameters (incl. regular expressions) and saving and loading of the filters. THis is particulary useful during behavioral analysis, because we can quickly view the most interesting activity only (process creation, file writes and registry changes). On the other hand, during more detailed analysis we can filter out “common activity” and focus on more suspicious malware artifacts and actions in operating system (e.g. process injection).
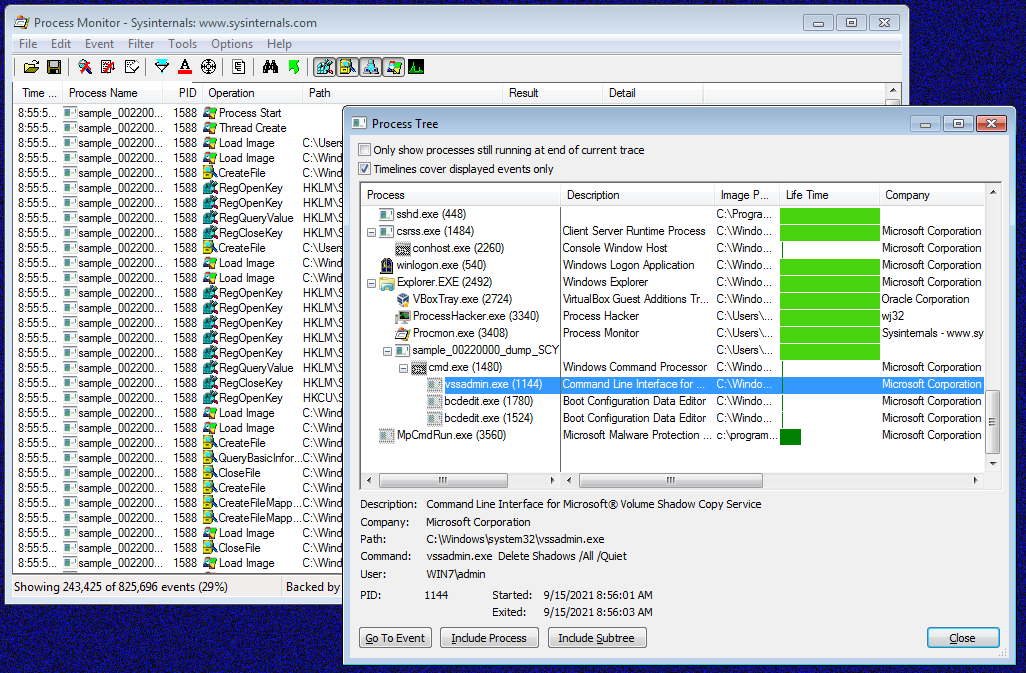
Fig. 5: ProcMon and REvil ransomware activity; it deletes volume shadow copies before file encryption
Additionally, Windows Sysinternals Suite contains more powerful tools, which are often used during malware analysis such as already mentioned Process Explorer, ProcDump, Autoruns, WinObj, DebugView and Strings. However, those tools are out of scope of this overview of Top10 malware analysis tools.
Conclusion
In this first part we have introduced 5 free tools which are suitable especially for analysis of native executable files (PE for OS Windows, or ELF for OS Linux). We also propose some alternatives or recommendations. In the second part of this overview, we would like to present tools suitable for analysis of other file types such as Office documents.