Introduction
IPv6 is an Internet Protocol version 6, that was made to replace IPv4. Like IPv4, it is intended for routing data over the Internet. Although, the version 6 protocol was introduced at the end of the nineties, it did not become a standard until 2017. Despite the fact that IPv6 already exists for such a long time, it still has not completely replaced its predecessor.
Advantages over IPv4
IPv4 was standardized in 1981, when the use of 32-bit addresses was a very logical and sufficient implementation. This means, that there are 2³² original IPv4 addresses available, which equals to more than 4 billion in decimal representation. Although this number may seem huge, it is clear that the original addresses will run out. For this reason, the IPv6 protocol was created, the address range of which is 128-bits, and thus the number of available unique addresses is significantly higher because of exponential growth nature.
In addition to the number of available addresses, IPv6 has other advantages. One of them is the Plug and Play functionality, which makes it easier for users to connect the device to the network, as the configuration is performed automatically after successful connection.
Another important part of the implementation is the so-called IPv6 Flow Label specification. Each IPv6 packet has a header, that contains three important information to this specification: source address, destination address and information about the flow to which this packet belongs. The protocol header format is shown in the following image:
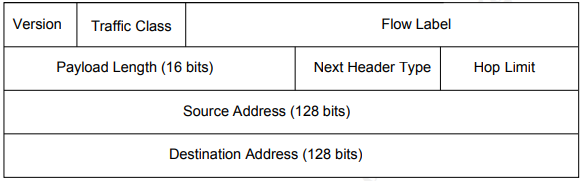
Figure 1 - Mandatory fields of IPv6 header
Flow Label field is used by a source to label the packets that belong to the same flow in order to request special handling by IPv6 routers. It is a flow of packets that have something in common and are sent to the same unicast, multicast or broadcast address. The correct assigning of packets in the flow is ensured by the nodes. A node is any device in the network, whether it is a router, a switch or an endpoint such as a computer. Thanks to the flow label, it is possible to identify multimedia data streams, such as TV or video conferences, which should have priority.
Unlike IPv4, IPv6 does not support in-transit fragmentation, which is both relatively resource-intensive and opens new possibilities for attackers e.g., in IPS/IDS evasion. If the router detects that the data is large, it discards it and sends an ICMPv6 message to the sender, because the source station can use the extension header to fragment the data into smaller ones. However, this is not possible during the sending process.
IPv6 Addresses
Example of IPv6 address:
2001:0db8:3c4d:0015:0000:0000:1a2f:1a2b
The address consists of 8 groups, each of which contains 4 hexadecimal digits. Hexadecimal system uses 16 distinct symbols: numbers from 0 to 9 and letters from A to F (represent values from 10 to 15). IPv6 addresses can be simplified or shorten. It is possible to use :: to represent a group, that contains 0000. It is also possible to skip zeros as long as they are at the beginning of groups. After editing, our example should look like this:
2001:db8:3c4d:15::1a2f:1a2b
Coexistence of Ipv4 and IPv6
Since it is not possible to switch from using IPv4 to IPv6 overnight, and there are still devices that do not support IPv6 addressing, there are 3 techniques that make version 4 and 6 interoperable.
Dual stack is implemented directly in the operating system. The systems have address stacks created in a hybrid form (they can also be separate). Hybrid stacks allow representing an IPv4 address in IPv6 format. Communication between nodes takes place using the new IPv6 protocol, as long as both nodes that communicate have an assigned IPv6 address. If one or both do not have such an address, communication must be done using IPv4. In essence, both IPv4 and IPv6 protocols can run simultaneously on some devices.
Encapsulation is the second way to connect these two worlds. It is a technique, where IPv6 packets are transmitted over the IPv4 Internet. An IPv6 packet is wrapped in an IPv4 packet, which is sent over a network with which it is compatible. It is decompressed at the destination node because it is marked as “encapsulated” in the header and continues down the network as an IPv6 packet.
In special case, when one device can only use the new protocol and the other can only use the old protocol, technique called translation is used. The role of the translator is therefore to mediate communication between two devices, that use different Internet protocols. Translation implementation is realized by adding temporary IP addresses, that are dynamically changed. Technically, this process is called Network Address Translation – Protocol Translation (NAT-PT) and it specifically translates IPv6 packets into IPv4 packets.
Security
The IPv6 protocol also includes IP security (IPsec), which represents a set of security specifications, that were created as part of the IPv6 implementation. It is a framework defined in RFC 2401.
Because the Internet is no longer a safe place, it became necessary to incorporate IPsec into the older version of the protocol. However, this implementation in the IPv4 protocol is optional and proprietary solutions prevail in it. On the other hand, IPv6 provides secure end-to-end communication thanks to IPsec, which means that the data is secured all the way from the sender to the chosen destination. It does not matter, that the data travels between nodes at all, it remains secure until it reaches its destination. In case of IPv4, such security is guaranteed only between border routers that are located between different networks.
IPsec also uses an important functionality called Authentication Header (AH). It is one of the so-called New Extension Headers. It is a way of ensuring data integrity and authentication for the entire IPv6 packet. AH also guarantees Anti-replay protection, which is a security element responsible for preventing an attacker from interrupting the original packet flow by intercepting the data packets and retransmitting them.
Authentication is an element that guarantees the recipient that the IP packet really came from the address that is written in the header and that the data flow has not been disturbed. Data integrity, in turn, points to the fact, that the data delivered to the recipient, was not modified by anyone during the journey. The entire format of this extension header for an IPv6 packet looks like this:
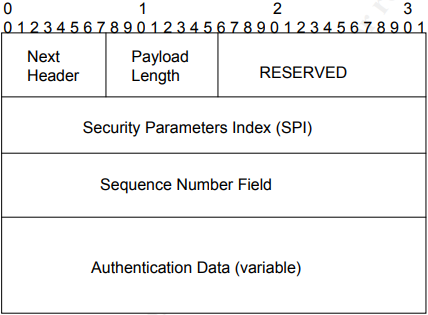
Figure 2 - Extension header of IPv6 packet
The Sequence Number Field can also be seen in the content of the header. This field contains a number, that ensures the Anti-replay protection which was mentioned above. The field is set to 0 when communication between the destination address and the sender has started. This number is always increased by 1, as long as one of the communicating parties is sending data. As soon as the receiver detects an IP packet that contains this field in duplicate, the packet is rejected. A duplicate of this field means, that an attacker has accessed the communication and modified and retransmitted the data.
IPv6 represents a big step forward in security over its predecessor. Nevertheless, even this protocol contains imperfections in its implementation. For example, the probability of an attack called Flooding is the same as with the IPv4 protocol. It is a DoS (Denial of Service) attack, in which the attacker tries to make the service unavailable to users, by sending a large number of requests to the server or to a certain part of the network and thus overwhelms it.
Conclusion
The implementation of the Internet protocol IPv6 certainly brought a number of advantages. But it is important to note, that the complete transition from the old protocol to the new one is not easy, and it will certainly take some time. Therefore, in addition to the replacement, the current challenge is the coexistence of these two protocols, while care must be taken not to violate the principles of safety and reliability.
