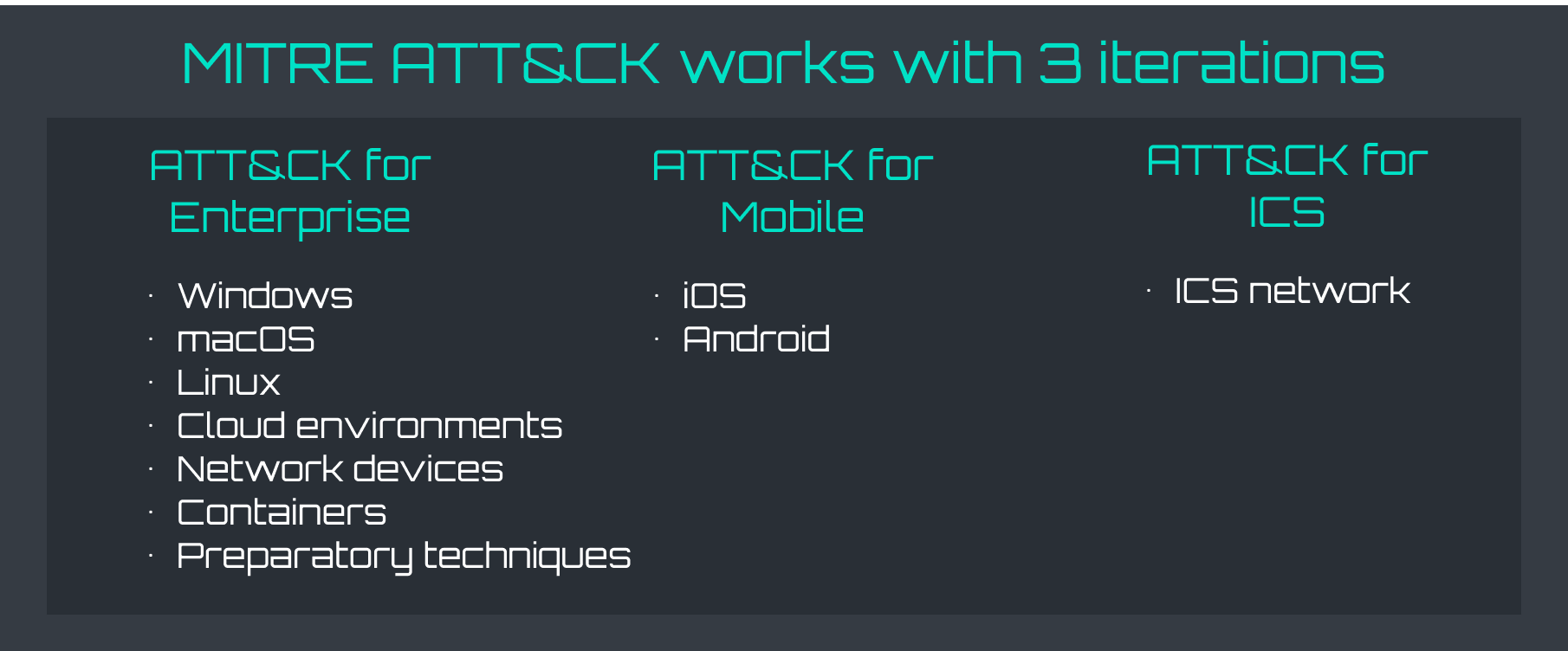
MITRE ATT&CK
The MITRE Corporation created the MITRE ATT&CK methodology for interpreting and describing cyberattacks. It gives a thorough and well-organized taxonomy of the numerous tactics and methods that attackers use to penetrate and control computer systems. Its name stands for “Adversarial Tactics, Techniques, and Common Knowledge.”
The framework is intended to assist companies in better understanding the methods and tactics performed by threat actors and implement effective defense strategies that can improve the detection and prevention of cyberattacks. It contains a wide range of strategies and methods from initial access through persistence, privilege escalation, and data exfiltration.
Cybersecurity experts, such as threat hunters, incident responders, and security analysts, regularly implement MITRE ATT&CK to identify and categorize cyber threats and to create efficient defensive measures to guard against them. In the battle against cybercrime and cyberespionage, it has become an essential weapon.
For better understanding, watch this short video, made by The MITRE Corporation, which is also published on their website.
For threat intelligence, incident response, red teaming, and tool selection, SOCs use the MITRE ATT&CK framework. SOC analysts may better understand the threat environment and spot possible flaws in their organization’s defenses by using the framework’s complete list of the strategies and methods employed by cyber attackers. The framework allows SOC analysts to instantly identify the type of attack occurring when an organization is vulnerable to a cyberattack and choose the right approach to mitigate it. SOCs can find vulnerabilities in their defenses and strengthen their security posture by simulating cyberattacks.
Cyber Kill Chain
The Cyber Kill Chain is a concept for interpreting the phases of a cyberattack, from the initial reconnaissance and weaponization of a threat through the delivery, exploitation, installation, command and control, and lastly to the activities committed by an attacker, including data exfiltration or other harmful actions.
An international security and aerospace corporation called Lockheed Martin was the first to establish the idea of the “Cyber Kill Chain” to help businesses better understand the phases of a cyberattack and create defenses against it.
Security professionals may more effectively identify and mitigate threats before they have an opportunity to cause significant damage by comprehending the various stages of a cyberattack. The Cyber Kill Chain is a popular concept for incident response and a tool for creating successful security policies to defend against attacks in the cybersecurity sector.
Such “chain” has 7 recognizable stages:
- Reconnaissance
- Collecting and analyzing data about target
- Looking for security vulnerabilities
- Weaponization
- Malware creation
- Creating ways for exploitation of discovered vulnerabilities
- Delivery
- Malware “injection” to the target’s system
- Exploitation
- Active execution of malicious code in the system by the usage of found vulnerabilities
- Installation
- Malware installation
- Gaining remote access to the environment
- Command and Control
- Command channels are using for remote console execution
- Maintaining and developing an attack
- Pursuing objectives
- Pursuing attack’s goals by the attacker
In conclusion, the Cyber Kill Chain focuses on the steps of a cyberattack, whereas MITRE ATT&CK focuses on the techniques and tactics employed by cyber attackers. These frameworks may be used together to better analyze and protect against cyber threats. They are both crucial instruments in the battle against cybercrime.
