Static application security testing (SAST) is a process that scans the source code of the application to identify bugs, security vulnerabilities, or other issues with the code. Unlike the opposite dynamic application security testing (DAST), this process merely parses and analyzes its source code without compiling or executing it.
There is a large number of both free and commercial tools that perform SAST. The goal of this blog is to take a quick, non-exhaustive look at some of them.
This article is organized into two main sections.
In the first section, we introduce large, well-known commercial SAST applications. They usually support many programming languages and frameworks and provide an intuitive graphical interface. Some provide limited demo or trial versions, but that is not a rule.
The second section describes some of the free offerings on the SAST market. These are smaller and simpler tools usually designed for only one programming language or bytecode. Also the free tools are usually command-line based.
Commercial Tools
SonarQube
SonarQube from SonarSource is a very well-known application. It is a full-blown web application with a friendly graphical interface. It also provides ways to integrate into various build tools, IDEs, and CI/CD pipelines.
The official distribution comes in three commercial variants and one open-source variant. Commercial versions of SonarQube have a large variety of security-related scan rules for many programming languages. That is one of the main selling points over the free version.
There is also a free distribution provided by OWASP that enhances the security-related rulesets of the free version of SonarQube. This distribution seems to be abandoned since 2019, though.
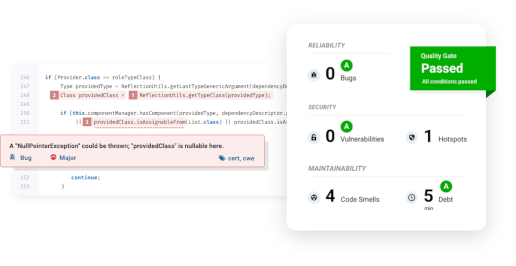
SonarQube by itself is not capable of checking the dependencies of the scanned application. Such a process is called Software Composition Analysis (SCA) or Open Source Analysis (OSA). There is, however, a free third party plugin that adds this capability to the SonarQube.
Personal Opinion
SonarQube is easy to install and easy to use. The free version is not very usable for serious security scanning - it is supposed to enhance the quality of code, not its security. It simply lacks many security rules. The paid version is, however, quite capable of security scans. The user interface is also intuitive and easy to navigate.
CxSAST
CxSAST from Checkmarx is an expensive product. The price corresponds with quality, though.
It is a fully commercial product with no free or trial versions. The only legal way to try it is to request a demonstrative presentation.
Unlike SonarQube, CxSAST is focused purely on code security scanning. Thus it is not trying to be a universal solution.
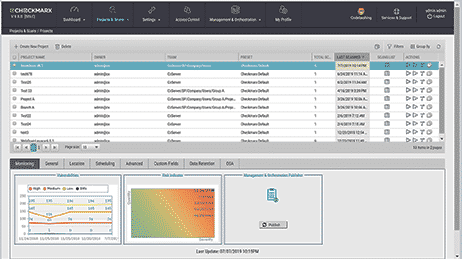
CxSAST is not capable of checking the application’s dependencies. There is a plugin for that called CxSCA.
Personal Opinion
CxSAST is quite cumbersome to install and activate.
Quality-wise it is a very capable product.
If you only seek to automate secure code review and not combine it with the quality code review, CxSAST may be a more appropriate solution than SonarQube.
Snyk Code
Snyk is a relatively new project. It serves primarily as an SCA/OSA application, at least in its free version. The free on-premise application is available on Github.
The paid plans also provide SAST capabilities. The author of this article, however, did not had the honor of using the paid SAST tool yet.
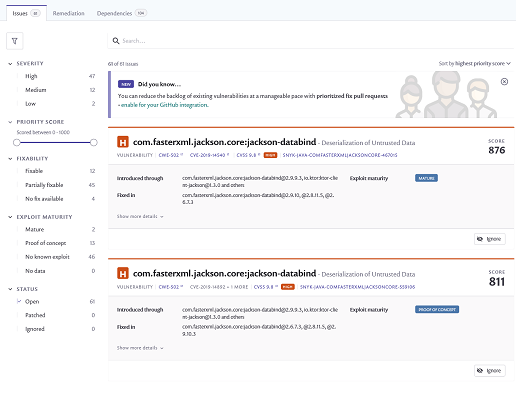
Snyk also provides a public repository of many known vulnerabilities in the open-source libraries.
Free Tools
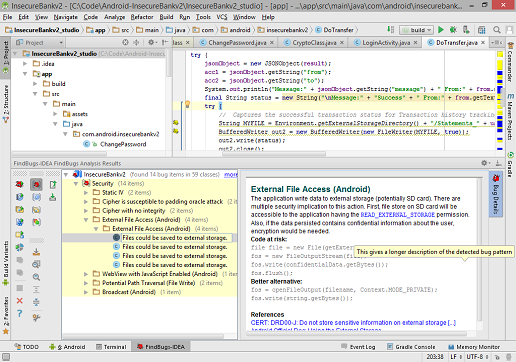
Find Security Bugs - Java
This project is a plugin for SpotBugs. It is developed as a standalone Java program, and it offers integrations with the most commonly used JVM build tools such as Ant, Maven, or Gradle. If used as a build tool plugin, it will display security-related bugs as compiler warnings.
This program scans Java applications and authors also provide plugins for Eclipse, IntelliJ IDEA, and Android Studio with tighter integration with IDE’s internal static analysis capabilities.
It supports many common vulnerabilities with dedicated care for typical Java application frameworks such as Spring MVC.
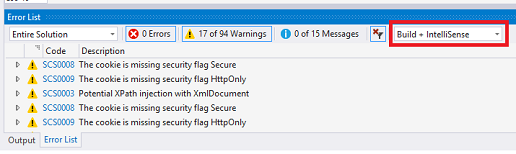
Security Code Scan - C#
Security Code Scan is an open-sourced project shipped as a standalone command-line application, Visual Studio Extension, or NuGet package. It can detect common vulnerabilities such as SQL Injections, Cross-Site Scripting, Cross-Site Request Forgery, and others.
It supports both the .NET Core and the now legacy .NET Framework, and it can be integrated into CI pipelines with dedicated support for Github and Gitlab.
Bandit - Python
Bandit is a command-line application distributed as a pip package.
It scans general-purpose Python code with support for popular web application frameworks such as Django.
Below is an example of a found security issue with Bandit. Scan reports can also be exported into various formats including html, xml, csv, json and others. Hence it can be quite easily integrated into CI/CD pipelines
...
>> Issue: [B301:blacklist_calls] Use of unsafe yaml load. Allows
instantiation of arbitrary objects. Consider yaml.safe_load().
Severity: Medium Confidence: High
Location: examples/yaml_load.py:5
More Info: https://bandit.readthedocs.io/en/latest/
4 ystr = yaml.dump({'a' : 1, 'b' : 2, 'c' : 3})
5 y = yaml.load(ystr)
6 yaml.dump(y)
...
phpcs-security-audit - PHP
phpcs-security-audit is an extension for PHP_CodeSniffer that provides security-related rules. It focuses on the standard PHP library and also provides special support for Drupal 7.
PHP_CodeSniffer is a standalone command-line application that parses and processes the source code of the target application. The official documentation also describes integration with Jenkins CI/CD.
$ phpcs --extensions=php,inc,lib,module,info --standard=./vendor/pheromone/phpcs-security-audit/example_base_ruleset.xml ./vendor/pheromone/phpcs-security-audit/tests.php
FILE: tests.php
--------------------------------------------------------------------------------
FOUND 18 ERRORS AND 36 WARNINGS AFFECTING 44 LINES
--------------------------------------------------------------------------------
6 | WARNING | Possible XSS detected with . on echo
6 | ERROR | Easy XSS detected because of direct user input with $_POST on echo
9 | WARNING | Usage of preg_replace with /e modifier is not recommended.
10 | WARNING | Usage of preg_replace with /e modifier is not recommended.
10 | ERROR | User input and /e modifier found in preg_replace, remote code execution possible.
11 | ERROR | User input found in preg_replace, /e modifier could be used for malicious intent.
...
Conclusion
In this article, we quickly introduced some of the more common SAST tools. The below table summarizes described SAST solutions.
| Solution | License | Programming Languages | SCA/OSA |
|---|---|---|---|
| SonarQube | Free+Paid | Many | Free Plugin |
| Checkmarx CxSAST | Paid | Many | Plugin |
| Snyk Code | Free Demo+Paid | Many | Yes |
| Find Security Bugs | Free | Java | No |
| Security Code Scan | Free | .NET Languages | No |
| Bandit | Free | Python | No |
| phpcs-security-audit | Free | PHP | No |
For more information, we recommend visiting this thorough OWASP article.
One needs to remember that the SAST tools are only a single part of a proper secure CI/CD pipeline. These are powerful tools that help to identify the security vulnerabilities in the application. We should mention that many SAST tools won’t scan the 3rd party libraries declared in the build configuration file. For that, you need so-called SCA or OSA tools. We may cover them in greater detail in some future articles.
As with all tools, SAST has some limitations. Automated scan reports produce contain a large number of false positives. They need to be manually reviewed by a code security specialist or, at least, by a skilled senior-level programmer.
SAST tools also cannot find all security issues. It is true, especially for vulnerabilities caused by faulty application logic. Such faults include improper authorization management, tenant isolation, etc.
Hence it is needed to complement static code checking with occasional dynamic application security tests (DAST) and penetration testing.
