
Social Engineering or People Hacking are terms often used for cyberattacks, where the target is primarily human, not the computer. There are more ways, how the attacker can gain access or information wanted. However, all of them relies on tricking human, with all the psychological knowledge and skills, that an attacker could have. This short video from Defcon conference is worth to watch, because it shows one type of social engineering attacks – vishing. It is a process, where scammer is trying to gain access to victims personal information by phone call.
Other interesting form of social engineering includes the process of dropping USB storage devices in public places, for example in company park or university campus. It is enough for one person to pick one and plug it into the computer and he can literally endanger every device in the network. USB device could contain malicious software, which might help the attacker to take control of the victim’s device or just to use keylogger (malware, which records keys pressed on the keyboards), to read confidential data.
Very similar, but not the same, is using USB cables in public places like airports, shopping centers or in public transport. These cables are made for powering up peoples’ devices, but it can be very tricky. Cables might have an advanced implant inside, which can install malicious software to your device, read communication and more. This is an EXAMPLE of such cable.
How to stay safe
- Never plug unknown USB/CD/etc. media into your device. Companies should have set the rule in their corporate policy, to not plug in any media at all.
- If there is no power in your device, use your own cable or borrow it from someone you trust.
- Never trust anyone, who call or email you and do not proof their identity to you. If a stranger claiming, that he works for your bank or company, it doesn’t have to be true. Always keep in mind, that no legitimate employee will ever ask for your password or other information that protects your account.
- “Look before you leap” is wonderful quote, that refers to be careful in every situation. Attackers could act very urgent in phone calls or emails and they might take an advantage of your bad decision in high-pressure situation.
Phishing is well-known and definitely not unusual type of social engineering. By definition, phishing is specifically described as the process of tricking victims, by sending them emails or text messages, which leads to malicious webpages or installing malware in victims devices, by using attachments. Most common way of online correspondence used are emails, but nowadays in the era of social media there are more often used phishing text messages. The whole process of trickery depends on gaining sensitive information from victim, mostly login details or credit card information.
Let’s imagine the scenario of scammer sending a malicious email, that urge you to quickly change your password of your social media account. Let’s consider, it could be an Instagram profile. In the email is often displayed a link, crafted button or attachment, which will take you right to the Instagram section, where you could safely change your password. Here is the whole trickery, the link won’t take you to the official website of the social media, but to the malicious website, which looks exactly the same. It is possible, for skilled attacker to make an exact clone of websites in few minutes. Same colors, same fonts, same text, everything the same. Only difference is that you won’t change the password, you only think that you did. But what actually happened, is that you unknowingly send your valid login information to the attacker and now, he has the power of taking the full control of your profile, messages and all data stored in that social platform.
One of the most alerting sign, that you are not in the legit website, is web-protocol. It is a very first part of URL address and it could look likehttp:// or https:// . The second protocol refers to a secure one and all of the legit websites will use it. If you want to log into some account and the URL address starts with http:// not https:// , myou can be sure, that the website is fake. This WEB might be a great example of how the fake bank website looks like.
Phishing attacks which are targeted to the credit card information could work the same. You may receive a message with malicious link, where you will write down your card number, expiration date and CVC code in assumption, that you are sending this information to your bank, or some bank employee.
Also as was mentioned before, besides a fake website, users should be careful about malicious attachments too. Just opening them could lead to installing a malware in their computer, which could lead to more and more problems. The question is, how you can avoid something like that?
Website addresses in emails are well adjustable as well as standard text. In the picture below is shown the example of how formatted link looks like + another important elements, that you need to pay attention.
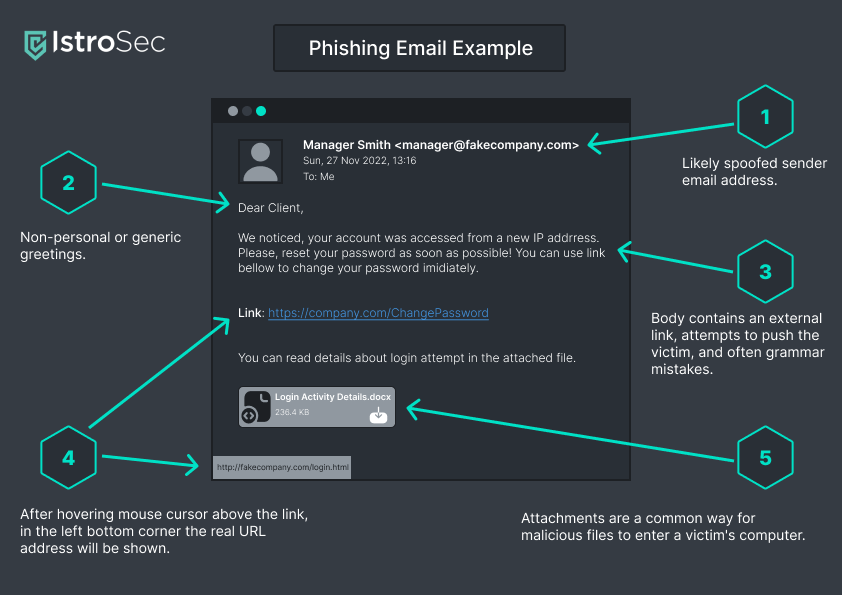
As you can see, when the mouse hover above the link, in the left bottom corner will be shown, where the link actually goes to. It is clear, that the blue link is different, from the actual URL address.
Another key fragment of analyzing phishing email is the domain name. That is the part of an email after the symbol @ . Scammers are using domain names, which are very similar to its original. As an example we can use [email protected] . This can be replaced for [email protected] . User also need to consider, that the domain name is also used in URL web addresses. For example the official Facebook domain name https://facebook.com could be changed by malicious actor for http://f.acebaok.com . Notice, that these two URL addresses and emails are very look alike, but they are not the same. Even when you open the fake website, design will look the same, but as was mentioned before, it is not the original website.
Now, you know, how to find suspicious things in email and here are few another tips, how to stay safe from phishing attacks:
- Do not open attachments from untrusted emails.
- Do not publish a personal information about yourself. (phone number and email)
- Do not click on embed links in email or messages. If you feel the necessity, to click on it, double-check the domain name , or type URL address manually.
- If you are prompted to change password, bank information or any kind of confidential data and you can’t decide if the link is legit, manually go to the website or use the application.
- Always report spam emails, and do not even open them.
- If the email body uses generic content, such as Dear Sir/Madam, it’s the red flag, because it is the typical characteristics for phishing email.
- Never open attachments with .exe, .src, .com or .bat suffixes.
- Be careful with common file types such as .doc(x), .xls(x), .zip, .pdf. Attacker could act as some trusted entity and send you file, which can infect your device.
It has all important attacks features as phishing, but it is more targeted to the small groups, or individuals. Because of the fact, that the target is specific group, the attackers could prepare better, and the phishing emails could be more trustable. This could lead to more specific email design, body content without grammatical mistakes, structured text, nothing general. When targets are especially high-ranking members of companies, politics or celebrities it is called whaling.
Defending against spearphishing attacks has the same rules as general phishing attacks. Users just have to be more careful, about who are the sender and what URL addresses and attached files they are going to open. Also, companies should consider, that spearphishing attacks are more relevant for them, that normal general phishing. That is why, company policy should set the rule, for 2 factor authentication, which could be by token, or hardware device, such as USB. It is worth to mention, that misconfiguration of such thing, could lead to even worst security. The very last and the most important part, always verify the identity of the person, through every means of communication!
These few sections should describe and show, how phishing attacks works, and how to be prepared for them. For your better understanding and better security awareness, we prepared an interactive test, which you will find in the next module. Good Luck!
Test
