OneNote, a popular note taking app, is a part of the Office 365 suite. This means it’s very prevalent on business computers, registered to open notebooks and ready to be abused. Additionally, and unlike other Office applications, OneNote does not feature Protected View. Without Protected View, files bearing the MotW (files downloaded from the Internet, or extracted from some archives), don’t get any extra security features.
With the discontinuation of macros, OneNote is the latest app to be abused by threat actors. OneNote allows attackers to embed executable files inside notebooks. The files itself are executed with a double-click, after confirming a security prompt.
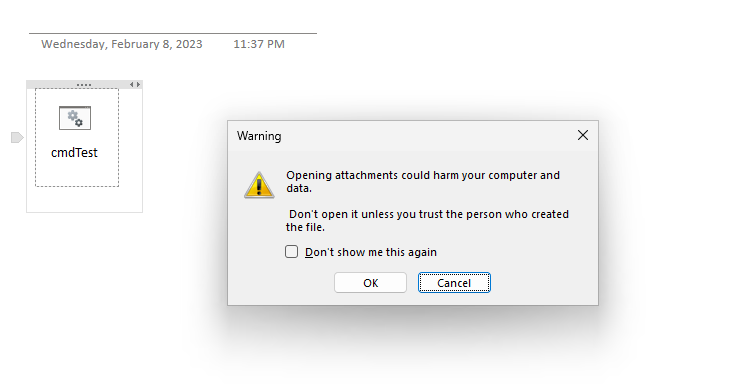
Figure 1. Prompt when executing files from OneNote.
Files itself are distributed mostly via e-mail. Common e-mail providers, like Gmail and Outlook, don’t block file attachments associated with OneDrive and OneDrive notebooks with embedded executables share the same file extension as other OneDrive notebooks.
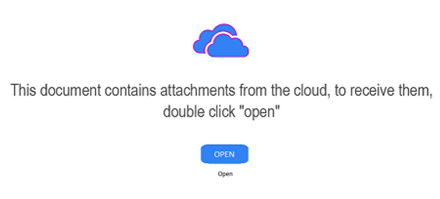
Figure 2. An example of a malicious document, with a social engineering aspect.
The most recent malicious campaigns consisted of embedding .cmd file, as well as .hta scripts. It is very likely that attackers will also experiment with other, more unusual file types.
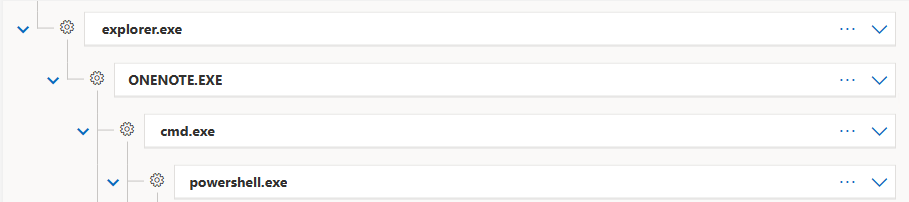
Figure 3. A campaign seen in-the-wild abusing an embedded .cmd file.
Detection
We recommend creating a high severity alert for any suspicious OneNote child process creation. We created the following SIGMA rule, which should alert on suspicious code execution attempts.
title: Microsoft OneNote Spawning Suspicious
status: experimental
description: Detects an unusual child process creation from Microsoft OneNote.
references:
- https://istrosec.com/blog/onenote-abusing/
author: IstroSec
date: 2023/02/09
logsource:
product: windows
service: sysmon
detection:
selection:
EventID: 1
ParentImage:
- '*\ONENOTE.EXE'
filter:
Image:
- '*\msedge.exe'
- '*\msedgewebview2.exe'
- '*\chrome.exe'
- '*\firefox.exe'
- '*\opera.exe'
- '*\brave.exe'
- '*\iexplore.exe'
- '*\WINWORD.EXE
- '*\EXCEL.EXE
- '*\POWERPNT.EXE
- '*\AcroRd32.exe'
- '*\Acrobat.exe'
- '*\ONENOTEM.exe'
- '*\OUTLOOK.exe'
- '*\ai.exe'
- '*\Teams.exe'
- '*\notepad.exe'
- '*\protocolhandler.exe'
- '*\ONENOTE.EXE'
- '*\splwow64.exe'
condition: selection and not filter
falsepositives:
- unknown
level: high
From our testing, legitimate use cases of OneNote spawn only processes of other Office applications, web browsers, PDF editors and ONENOTEM.exe. Therefore, the SIGMA rule should create very little to no false positives, although further testing in your environment is necessary.
Alternatively, if you use Defender for Endpoint without SYSMON in your infrastructure, you could use the following query:
DeviceProcessEvents
| where InitiatingProcessFileName == "ONENOTE.EXE" and not ( FileName in~ ('protocolhandler.exe','notepad.exe','Teams.exe','powerpnt.exe','ai.exe','msedge.exe','msedgewebview2.exe','chrome.exe','firefox.exe','opera.exe','acrobat.exe','brave.exe','iexplore.exe','winword.exe','excel.exe' ,'AcroRd32.exe','ONENOTEM.EXE','OUTLOOK.EXE',’ONENOTE.EXE’,’splwow64.exe’))
Or with SentinelOne hunting query:
SrcProcName = "ONENOTE.EXE" AND TgtProcName Not In ("msedge.exe","msedgewebview2.exe","chrome.exe","firefox.exe","opera.exe","brave.exe","iexplore.exe","WINWORD.EXE","EXCEL.EXE","POWERPNT.EXE","OUTLOOK.EXE","AcroRd32.exe","Acrobat.exe","ONENOTEM.EXE","ai.exe","Teams.exe","notepad.exe","protocolhandler.exe","ONENOTE.EXE","splwow64.exe")
Prevention
Code execution from OneNote can be prevented with child process creation blocking. This can be achieved with multiple solutions.
Attack Surface Reduction
Attack Surface Reduction policies is a built-in security feature into Windows 10 and Windows 11 and requires Windows Defender or Microsoft Defender for Endpoint to be running with real-time protection enabled.
ASR policies allow you to block child process creation from Office apps. The specific rule name is: “Block Office application from creating child processes”. The policy can be enforced via Intune, Configuration Manager or GPO.
You can enable the policy with the following GPO:
GPO path: Computer Configuration\Administrative Templates\Windows Components\Microsoft Defender Antivirus\Microsoft Defender Exploit Guard\Attack Surface Reduction\Configure Attack Surface Reduction rules
Add the following GUID into the table d4f940ab-401b-4efc-aadc-ad5f3c50688a with value 1, representing block mode.
Note: The ASR policy will apply to all Office applications, not just OneNote. Expected FPs include blocking the execution of browsers and other legitimate applications from Office apps.
Exploit Guard
Microsoft Defender Exploit Guard allow to block child process creation, but unlike ASR, the policy can be applied to just specific applications. As with ASR, Exploit Guard is built-in into Windows 10, Windows 11 and requires Windows Defender or Microsoft Defender for Endpoint to be running with real-time protection enabled.
Child process creation can be blocked via Exploit Guard with the following methods:
Set-ProcessMitigation -Name ONENOTE.EXE -Enable DisallowChildProcessCreation
For a deployment via GPO, you can use the following XML config file:
<?xml version="1.0" encoding="UTF-8"?>
<MitigationPolicy>
<AppConfig Executable="ONENOTE.EXE">
<ASLR ForceRelocateImages="true" RequireInfo="false" />
<ChildProcess DisallowChildProcessCreation="true" Audit="false" />
</AppConfig>
</MitigationPolicy>
That must be deployed to a location accessible to all endpoints and set via the following GPO:
GPO path: Computer Configuration\Administrative Templates\Windows Components\Microsoft Defender Exploit Guard\Exploit Protection\Use a common set of exploit protection settings
