The overall state of IT security can be described as never-ending wild arms race between attackers and defenders, vying for control over the single most valuable thing organizations possess – data.
Advanced types of cyberattacks permeated from the arsenal of state-sponsored actors into the toolset of organized crime groups focused purely on financial gain. Existence of such advanced persistent threats means that even organizations with mature cybersecurity practices can fall victim.
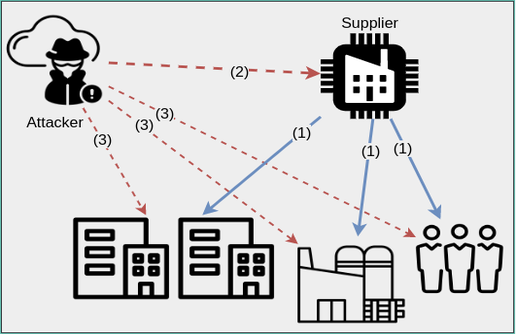
Supply chain attack is a typical example of an attack requiring high technical skills, significant persistence, and patience. It’s essence also explains why is so difficult for organizations to defend against. This problem and the need of information and cyber security within the supplier-customer relationship has manifested itself in the form of ISO 27036 standard, one of many from the ISO 27K series.
Anatomy of a supply chain attack in general consists of a compromise of a supplier-type organization, malicious tampering with its software product source code and subsequent distribution of the malicious version to the customer environments via standard update channels. All known to date supply chain attacks have these in common. In 2015, a malicious variant of Apple’s Xcode IDE was discovered, dubbed XCodeGhost, with backdoor and C2 functionality. In 2017 it was the global incident with NotPetya, which was initially distributed via an update to a commercial accounting software used in Ukraine. December 2020 made history because of the SolarWinds incident, when a malicious backdoor functionality was discovered in the Orion software. The incident itself began with an undetected compromise of the supplier as early as September 2019, with the malicious Orion version being distributed to customers since March 2020.
Organizations routinely buy software and technical equipment to perform their business activity. Often overlooked but particularly important is the fact, that by deploying a product from a third party we move a part of the client organization’s security into the hands of the supplier.
Organizations that are lucrative targets for the attackers typically have good security according to current standards and best practices, which raises the amount of resources and time needed to perform a successful cyberattack. Sophisticated attackers, even though they often have significant resources at their disposal, also want to use them effectively. In the supplier chain of the targeted organization or industry sector, they identify the relatively weakest link in terms of cybersecurity and focus their primary attack there. Attackers have the advantage of a multiplication effect, when a successful compromise of a single supplier can turn into compromise of many organizations further down the supply chain.
Standard cybersecurity practices, monitoring of network traffic, endpoints and logs cannot guarantee stopping such an attack, because the actual moment of compromise is not accompanied by typical attack manifestations. It comes quietly and unexpectedly via a trusted channel.
Most recently, the IT world was shaken by an incident revolving around a product from Kaseya for remote managements and monitoring (RMM) of endpoints. The Kaseya VSA (Virtual System Administrator) software is used by organizations offering managed IT services (MSP) for the end-customers. The Kaseya incident differs from the previous ones by the fact, that the impact in form of REvil ransomware reached the victims via two suppliers.