
As part of the comprehensive provision of an adequate level of security, it is necessary to reflect on new threats, verify the complexity and systematicity of implemented security measures, as well as detect the level of resilience of the organization to threats and attacks relevant to the organization.
IstroSec provides the following offensive services for individual types of organizations and according to the customer’s needs:
Why IstroSec?
Skills of the IstroSec experts in the field of offensive security are supplemented by holding certificates such as OSCP, OSWP, CRTP, CRTE, GXPN, CEH and others, along with years of experience. They performed offensive security services for clients from the FORTUNE 500 group and other commercial and multinational organizations.
Vulnerability assessment
As part of vulnerability assessment, experts from IstroSec perform vulnerability scans using automated tools (commercially available as well as self-developed for this purpose). Vulnerabilities that cannot be detected in an automated manner (especially business logic vulnerabilities, vulnerabilities that need to be identified based on a comprehensive assessment of the environment, and others) are identified manually.
After the identification of vulnerabilities, it is verified whether these are not false-positive and vulnerabilities are assessed in unity also in relation to other vulnerabilities.
When assessing vulnerabilities, exploitation of the vulnerabilities is not part of the process.
IstroSec offers:
-
External vulnerability assessment
-
Internal vulnerability assessment
-
Cloud vulnerability assessment
-
Vulnerability assessment of application or application endpoint.
Vulnerability assessment should be performed according to the type of organization:
-
Continuous (for organizations with high security requirements)
-
Once per month (for organizations with increased security requirements)
-
Once per 6 months (for organizations with standard security requirements)
-
Once per year for other organizations
Why IstroSec?
Our experts are skilled with the necessary tools and have plenty of experience with interpreting their output. Continuous enrichment of knowledge about current cyber threats allow them to create tailored and effective recommendations that help to improve the client organization’s security posture.
Vulnerability Assessment program
For some organizations, due to their security requirements and security profile, it is appropriate to build their own vulnerability assessment program.
The program consists of the following components:
-
Infrastructure analysis and vulnerability assessment program design
-
Implementation of technical prerequisites for the vulnerability assessment program:
-
test equipment (network and application vulnerability scanners)
-
automation of evaluation
-
-
Design and implementation of vulnerability assessment processes
-
Training of specialists to perform vulnerability assessment
-
Design and implementation of program development processes
Penetration Testing
Penetration testing (ethical hacking) is the authorized intrusion into a customer’s networks, applications, or infrastructures to assess the level of security of these components from an attacker’s perspective. In contrast to vulnerability assessment, penetration tests include exploitation of identified vulnerabilities, post-exploitation (assessment and testing of the possibilities that an attacker can exploit on a system in tested network or infrastructure), lateral movement within the permitted scope and search for other vulnerabilities and re-exploitation.
IstroSec offers:
-
External penetration test:
-
Web applications and application endpoints
-
Network penetration test
-
Social engineering (phishing, spearphishing, smishing, vishing)
-
-
Internal penetration test:
-
Application penetration test
-
Network / Infrastructure penetration test
-
Penetration test of Active Directory
-
-
Cloud penetration test
-
Mobile application penetration test
-
Wireless network penetration test
IstroSec also offers:
-
Goal-oriented penetration test. The goal of this type of engagement is not to completely compromise devices or find as many vulnerabilities as possible, but to verify whether an attacker is able to perform any particular activity in the system (for example, access a specific database, modify a domain policy, or disable an IoT device)
-
Scenario-based penetration test. Scenario-based penetration tests aim to verify the effectiveness of implemented measures against specific tactics, techniques and attacker procedures (TTP)
Why IstroSec?
IstroSec experts have plenty of experience with performing penetration tests of internal infrastructure and a wide variety of applications, including cloud-hosted. Their creativity has resulted in discovery of multiple new vulnerabilities and ways of exploiting them.
Red Teaming
Red team engagement uses – based on security profile of the company - real tactics, techniques and procedures (TTP) in order to simulate real cyber threats. Goal of red team is to not only to verify the level of cybersecurity within organization, but also to help the defending team detect and react to cybersecurity incident.
Red team objective is to simulate real life attack against organization. Attack is based on relevant threats and TTPs for the targeted organization. During simulation the goal is to verify the security procedures, technologies, designated security team and identify potential deficiencies. Red team is usually done without the knowledge of security team, with the exception of selected employees.
Phases of Red team:
-
Creating threat profile for the organization
-
Passive and active information gathering
-
Passive reconnaissance (including OSINT and DarkWeb search)
-
Active reconnaissance
-
-
Set up attacks with specific goal in mind – such as access to specific data, taking over the infrastructure, compromising specific user, running code on the devices etc.
-
Initial vector of attacks usually comprise of:
-
Attacks against user (social engineering)
-
Attack on user devices
-
Attack against organization perimeter
-
Attack on remote assets (mainly cloud services)
-
(optional) physical security
-
(optional) attacks on the supply chain
-
-
Drafting report of attack (successful and unsuccessful attacks) and steps taken to accomplish set goals. Most of the time the steps consists of:
-
Escalating privileges on devices, systems and following post exploitation activity on said devices or systems
-
Distribution of attack tools or specially crafted malicious code – based on the scope of set goals
-
Lateral movement across systems
-
Another steps depending on the specific requests from organization
-
-
Creating red team report which consists of:
-
Successful vectors of attack
-
Identified vulnerabilities within organization
-
Countermeasure recommendations
-
Time line of red team activities
-
Assessment of efficiency of implemented measures
-
Why IstroSec?
Apart from high qualification in performing penetration tests themselves, IstroSec experts closely study tactics, techniques and procedures used by the attackers in practice. This combination allows the client to safely test their resiliency and preparedness for real cyberattacks.
Purple Teaming
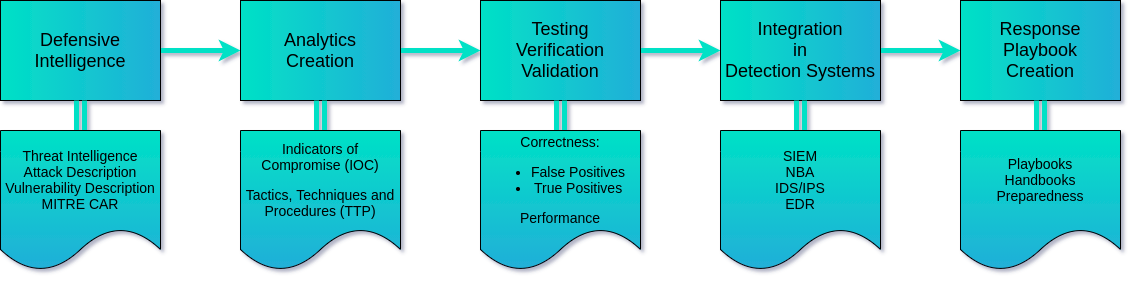
Purple teaming methodology
For organizations with increased standards for security and organizations which are target of advanced attacks on a long-term basis. There is a need to implement security procedures and monitoring which can respond to current threats.
During purple team engagement team at IstroSec focuses on people, processes and technologies. Based on this approach IstroSec will:
-
Create necessary procedures/guidelines for purple teaming
-
Educate internal security team
-
Suggest and implement needed technologies
-
Identify relevant assets and implement analysis based on predefined methodologies




